Personal Certificate Import Utility for Pocket PC 2003 and Windows
Mobile
There is now a much
easier way to import a certificate. You can import
a certificate directly
from a PKCS#12 or PFX file ("P12imprt"). Source
code available under the GNU Public License.
|
1.1 Introduction
I have made Crtimprt, a program for Pocket PC 2003, Windows
Mobile 5.0 and Windows Mobile 6. It allows you to import: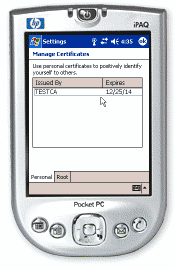
- A "Personal Certificate" issued by any Certificate Authority (CA).
- A private key which corresponds to this certificate.
- One, zero or more "Root Certificates".
Once an X.509 personal certificate is installed, you can use it to for
user
authentication on the Pocket PC. The imported certificate can be used
in the following
scenarios:
- User authentication in L2TP/IPsec VPNs.
- Web client authentication in Pocket Internet Explorer (SSL,
HTTPS).
- User authentication in 802.1x wireless networks (EAP-TLS only).
- Microsoft Office Communicator Mobile Client (press
release).
- Other third-party applications that happen to support Personal
certificates.
(Skip the smalltalk, get me straight to the
installation
procedure!)
The page that you are now reading describes how you can import a
certificate
and corresponding private key to Pocket PC 2003 (including Second
Edition), Windows Mobile 5.0 or Windows Mobile 6. The reason I
made the Crtimprt program was that I wanted to connect
with Pocket PC 2003 to a Linux VPN Server. It turns out
that Crtimprt can be used for other purposes too. The program is
based on the ENROLL sample code included with Microsoft's
"Software Development Kit (SDK) for Windows Mobile 2003-based Pocket
PCs". Kiko Vives
Aragonés and Antonia Saez Bernal have made a similar program
called PPCCertImport which is not based on Microsoft sample
code.
You can find it on Kiko's webpage.
You do not need Crtimprt (or P12imprt or PFXimprt) in the scenarios
that are listed here.
Make sure that what you want to achieve is not listed there, otherwise
you will be doing a lot of work and it will be all for nothing!
Crtimprt has been tested on a number of Pocket PC devices (see list below). I do not own a Pocket PC myself so I'm
interested in both positive and negative feedback, especially if you
tried Crtimprt on a model not listed below. Let me know if
it worked or not!
Here is a schematic of the procedure for importing your PKCS#12 (a.k.a.
PFX)
file to Pocket PC 2003 or Windows Mobile. All steps except
the last one are executed on
your PC with OpenSSL.
+--->
usercrt.pem ----+---> usercrt.p7b
......
|
|
: (crtimprt.exe)
user.pfx ----+---> cacrt.pem
----->+
:---------------> Pocket PC
|
:
+---> userkey.pem --------> userkey.pvk
.....:
My other program P12imprt
is much
easier to use. The P12imprt procedure is:
(p12imprt.exe)
user.pfx
-------------------------------------------------------------------->
Pocket PC
1.2 Author
The author of this document is Jacco de Leeuw (contact me).
Corrections, additions, extra information etc. are much appreciated.
2. Contents
3. Background information
Pocket PC 2003, Windows
Mobile 5.0 for Pocket PC, and Windows Mobile 6, which are often
abbreviated to WM5.0 and WM6 respectively, are based on a light-weight
variant of Windows called
Windows CE.
As
mentioned in the introduction, there are three main applications of
Personal Certificates: L2TP/IPsec, EAP-TLS and web
client
authentication.
Read this
section on the
P12imprt webpage for more background information.
Back to Contents
4. Obtaining a certificate and a
private
key
Read this
section on the
P12imprt webpage if you don't know how to obtain or create a personal
certificate and corresponding private key.
Back to Contents
5. Converting the certificate(s) and
private key
Your certificate is probably in
one of these three formats:
- One single PKCS#12 file containing private key and
certificate(s). In that case, you need to extract
these first from the PKCS#12 file before continuing with the next steps.
- Private key is in a PEM file. Certificate(s) are in other PEM
file(s). This is often so when the keys are generated with OpenSSL. In
that case, you can skip the PKCS#12 extraction step and go straight to
the PEM conversion.
- Certificate requested from Microsoft Certificate Services:
private key is in PVK format. Certificate(s) in .cer/.spc format(?). In
that case, you're almost set. You can skip most
of
the conversion steps.
Before you can import your certificate with Crtimprt you will need to
convert it to an intermediate format.
5.1 Extracting from PKCS#12
If your certificate is in PKCS#12 format, you will have to extract
several components from the PKCS#12 file. You will need OpenSSL for that. It is free and
included with many Unix/Linux versions and Cygwin. If you
prefer to use Windows or if you don't have access to a Unix/Linux
system, you can use the Windows
version of OpenSSL. In that case, download
the Win32 OpenSSL
Installer (get version 0.9.7 or higher). It will install the
OpenSSL
files to C:\OPENSSL. The OPENSSL.EXE executable
will
be in the BIN directory. It is probably a good idea to add
this
directory to the PATH variable if you are running Windows:
set PATH=%PATH%;C:\OPENSSL\BIN
|
PKCS#12 files often have the extension .p12 or .pfx.
So, let's assume that your PKCS#12 file is called user.pfx.
If the name is different replace user.pfx with whatever the
name is of your PKCS#12 file. Open a DOS Command Prompt and execute the
following commands
(lines starting with '#'
are comments and should not be entered):
# (Tip: use copy and paste for these commands)
#
# Extract the user certificate contained within the PKCS#12 file:
openssl pkcs12 -in user.pfx -nokeys -clcerts -out usercrt.pem
# Extract the CA certificate(s)
contained within the
PKCS#12 file:
openssl pkcs12 -in user.pfx -nokeys -cacerts -out cacrt.pem
# Extract the private key contained within the PKCS#12 file.
# (Warning: the resulting file userkey.pem is
not encrypted!
# Don't keep it around for longer than strictly needed!).
openssl pkcs12 -in user.pfx -nocerts -nodes -out
userkey.pem
|
5.2 Converting from PEM
At this stage I assume you have three PEM files called userkey.pem
(private key) , usercrt.pem (the user certificate) and
cacrt.pem
(the CA certificate(s)). PEM is a text based format, Base64 encoded. The
private key will have to be converted to
PVK, a Microsoft
proprietary format. The certificates are to be converted into PKCS#7.
For the PVK conversion,
you need the pvktool utility by Dr. Stephen N. Henson, who is
a
member of the OpenSSL team. He
has
reverse engineered the PVK format. Unix/Linux source code and a Windows
version of the PVK program are available on his PVK information
page. For your convenience I have made the following RPMs, in case
you run Linux. They have been signed with my PGP
key. The upcoming OpenSSL version 0.99 will contain support for PVK
files, so if you use that version you do not have to use the pvktool
utility.
The three PEM files are converted to the intermediate
formats
with
the following OpenSSL commands:
# Convert the certificate files to PKCS#7:
# (Note: the second keyword is crl2pkcs7 and not cr12pkcs7. Lower case
L.)
openssl crl2pkcs7 -certfile usercrt.pem -certfile cacrt.pem
-nocrl
-outform PEM -out usercrt.p7b
# Convert the private key file
from PEM to the Microsoft
# proprietary PVK format (use pvktool utility mentioned on webpage).
# (Warning: the resulting file userkey.pvk is not encrypted!
# Don't keep it around for longer than strictly needed!).
pvk -exc -in userkey.pem -topvk -nocrypt -out
userkey.pvk
|
New in Crtimprt v0.3 is that the parameter -exc is required (see below).
5.3 The result: files in PVK and PKCS#7
format
You should now have two files: a PVK file and a PKCS#7 file. If the
PKCS#7 file is
not in PEM format (text) but in binary DER
format (because you obtained
it directly from Microsoft Certificate Services), you will need to
convert it to PEM first. You can skip this step if you used the crl2pkcs7
command from the previous section.
# OPTIONAL: not needed if you
are converting from a PKCS#12 file.
#
# Convert PKCS#7 from DER
to PEM.
openssl pkcs7 -in usercrt.cer -inform DER -outform PEM -out usercrt.p7b
|
At this stage I assume you have a PVK file called userkey.pvk
and a PKCS#7 file in PEM format called usercrt.p7b.
The next step is to import these files with Crtimprt.
Back to Contents
6.1 Downloading Crtimprt
"Crtimprt" consists of a Pocket PC 2003 ARM executable called crtimprt.exe
and an (optional) configuration file called crtimprt.cfg.
They
are distributed in a zip file. The zip file also contains a sample
certificate file usercrt.p7b, a sample private key file userkey.pvk
and my source code (a patch, actually).
All zip files have been signed with my PGP
key.
(Warning: never use my sample certificate on a live
network and expect things to be secure. You have the private key, but
so does everybody else!)
6.2 Changelog
The CHANGELOG can be found here.
The only change between v0.3 and v0.2 is that the default "key spec"
has changed from AT_SIGNATURE to AT_KEYEXCHANGE.
What this means for you is that personal certificates imported with
Crtimprt v0.3 can now also be used with S/MIME secure e-mail. Note that if
you are upgrading from Crtimprt v0.2 to v0.3 you will probably have to write a new .pvk file. Otherwise you may get
the error message: "Private key type differs from DW_KEY_SPEC".
Back to Contents
7. Using Crtimprt on Pocket PC 2003 /
Windows Mobile
Here is how to use Crtimprt to import private keys and certificates to
the Pocket PC:
- Transfer the files userkey.pvk
and usercrt.p7b to the "My Documents" folder on your Pocket
PC (you can use any method to do the transfer: ActiveSync, a flash
memory
card, Bluetooth, infrared etc). The actual pathname of the folder
depends on the language version of your Pocket PC.
In the English version, it is "\My Documents", the German
version uses "\Meine Dokumente", etc.
- Transfer crtimprt.exe and crtimprt.cfg to the
Pocket PC. (The crtimprt.exe file is a Windows Mobile
executable, not a Win32 executable. You can't use it on your desktop
Windows computer).
- Edit crtimprt.cfg on the Pocket PC (or on your desktop
PC before you transfer it). If crtimprt.exe cannot find this
configuration file, it will use hardcoded settings (which are the same
as those in the sample crtimprt.cfg).
- The "key container" name has to be
different for every different
certificate that you want to import to the PPC. So if you want to
install only one certificate, you can use the default name "crtimprt".
But if you want to install another certificate for use with a different
VPN server, you need to modify the KEY_CONTAINER_NAME=
variable
before you run crtimprt.exe the second time.
- Set KEY_FILE= to the path and filename of the private
key. The default is userkey.pvk in the "My Documents" folder.
The actual pathname depends on the language version of your Pocket PC.
In the English version, it is "\My Documents", the German
version uses "\Meine Dokumente", etc.
- Set CERT_FILE= to the path and filename of the
certificate file. The default is usercrt.p7b in the "My
Documents" folder.
- Run crtimprt.exe by tapping
it in File Explorer.
(File Explorer does not show extensions. You need to pick the one that
is larger in size).
- You should see the message "Cert
Has Been Added
Successfully".
View the certificates that were imported to the Pocket PC
device:
- In the Settings menu, tap the "System" tab. Then tap "Certificates".
- Select the "Personal" tab if it has not been selected already.
The top of the page should say: "Use personal certificates to
positively identify yourself to others."
- You should see the newly
added certificate.
- If you tap on the name of this personal certificate, you should
see its details.
Tap "OK" to return to the previous window.
- Tap on the "Root" tab. You should now see the new root
certificate that you
added. If you tap on the name of this root certificate, you should see
its details.
Use File Explorer to delete the files userkey.pvk and usercrt.p7b
from both the Pocket PC and the desktop PC. They are not strictly
needed
anymore,
now that they have been imported to the PPC. You might also want to
delete userkey.pem on the desktop PC because it too contains
an
unencrypted private key.
Back to Contents
8. Status of Crtimprt
The current status of Crtimprt is as follows. I received reports that
Crtimprt works on (at least) the following Pocket PC 2003, Windows
Mobile 5.0, Windows Mobile 6 and Windows
CE devices:
- Acer N10
- AnexTEK SP230 / Audiovox PPC4100
- Asus MyPal A620
- Dell Axim X5 / Axim X30 / Axim X50v
- Fujitsu Siemens Pocket LOOX 600 / 720
- HP iPAQ 1930 / 1940 / 2210 / 4150 / 4155
- HP iPAQ hx2410 / rx3115 / rx3417 / rx3715 / hx4700
- HP iPAQ 3835 / 3850 / 3870 / 3950 / 3970
- HP iPAQ 5450 / 5455 / 5550 / 5555
- HP iPAQ 6150 / 6315 / 6340
- HTC Himalaya (i-mate / Qtek 2020 / O2 XDA II /
T-Mobile MDA II /
Vodafone VPA / Orange SPV M1000)
- HTC Blue Angel (i-mate PDA2k / Qtek
9090 / O2 XDA III / T-Mobile MDA III / Vodafone VPA
III / E-plus PDA III / Siemens SX66 / Audiovox 6601)
- HTC Magician (i-mate JAM / Qtek S100 / O2
XDA II Mini / T-Mobile MDA Compact / Orange SPV M500)
- HTC Universal (i-mate Jasjar / Qtek 9000 / O2 XDA Exec
/ T-Mobile MDA Pro / Vodafone VPA IV / Orange SPV M5000)
- Psion
Teklogix WORKABOUT PRO
- RoverPC S1
- Samsung SCH-i730
- Symbol MC50
- Symbol MC9090G running Windows CE 5.0
- Symbol VC5090 running Windows CE 5.0
- Toshiba e750 / e805
If Crtimprt does or does not work on your Pocket PC, it would be great
if you could contact
me,
especially
if your model is not listed above! Note that some
Smartphones are software locked, so Crtimprt may not work on your
Smartphone even if the generic model is listed above. Please state your
cellular network if you contact me to report success or failure!
Importing password protected PVK files is not
supported. I think it is not too difficult to support, but at this
stage
I did not want to bother. According to Dr. Henson, the PVK encryption
is weak
anyway. I noticed that Pocket PC does not ask for a password when it
needs the private key to set up a VPN connection. So if your PPC gets
stolen, the perpetrators can abuse your client certificate to gain
access (that's why it is a bad idea to have the PPC remember your VPN
password such as in this
screenshot). Microsoft has been notified of this problem but it is
unknown if and when they will fix this.
By default, I use the extension .p7b for certificate files.
On
desktop Windows this extension is reserved for PKCS#7 files in DER
format (binary). However, I use it for PKCS#7 files in the PEM format
(which is base64 text). I do not know what the "standard extension" is
for PKCS#7 files in PEM format, so I simply picked .p7b. File
Explorer on desktop Windows shows files with this extension as
certificate icons, but if they are in PEM format you cannot import them.
Once the certificate(s) and the private key were imported, I could make
L2TP/IPsec connections with the Pocket PC emulator to Openswan and
Windows Server 2003. (Windows 2000 Server not tested but I assume it
works with Pocket PC hardware. It will not work with the emulator
because Windows 2000 Server does not support NAT-Traversal). I also
received reports that imported certificates can be used for client
authentication to websites.
Back to Contents
9. Troubleshooting
In case the program reports an error: here is a list of Windows CryptoAPI
error codes. These are probably not very helpful if you are not a
programmer.
Contact me by e-mail if you really can't get it working.
9. 1 Problem: "Unable to add Root Cert to Root
Cert store"
Some users reported an error when importing their
certificate ("Unable to add Root Cert to Root Cert store").
The Personal Certificate was imported but the Root
Certificate was not. This happens when the Root Certificate
Store is locked by the device vendor. The Personal Certificate is
installed but without a matching root certificate it will not be valid.
Especially Smartphones are prone to this problem: adding a Root
Certificate is a "privileged
operation". This means that your Smartphone may not only have a
hardware lock (SIM lock, provider lock) but also a software lock!
Telecom
operators and Smartphone manufacturers do not want you to install
applications that are not
approved by them. They claim that it is for your own good, so that
viruses cannot run on your device and run up your phone bill. This is
all part of the whole Digital Rights Management /
Trusted Computing situation that you already see on the Xbox and
Windows Vista as well. In the future you can expect to see this problem
more and more
if vendors get their way with this. To solve your
problem, you might have to
contact your operator to unlock your device. For instance, Orange has
an unlock
page for their SPV. More information can be found on the Smartphone2000
website. Microsoft has a Knowledge Base article
Q841060
where you can download a utility called SPAddCert, but they too refer
you
to your mobile operator if the Smartphone happens to be
software-locked.
Some device manufacturers do not supply an unlock utility but they do
provide a (signed) Registry editor with which you can unlock the
device, for instance the HTC
models (i-mate, Qtek, XDA etc.). An alternative would be to buy a
personal
certificate from one of the 5 'standard' root CAs in the certificate
store (Cybertrust,
GlobalSign, Entrust, Thawte, Verisign).
Unfortunately this alternative will probably not work because it seems
that those 5 root certificates are used to issue server certificates,
not personal certificates.
Windows Mobile based Smartphones won't even run executables or .cab
files unless they are signed. That means you will not be able to
install your own root certificate or run Crtimprt on these
Smartphones. In an MSDN blog entry called "How can I add root certs to
my Windows Mobile device?", Microsoft writes:
"We have definitely gotten the message that a lot of customers
find themselves in this situation and we feel your pain." Ha! We
feel your pain... what a right bunch of hypocrites!
9.2 Problem:
"CertFindCertificateInStore failed"
You run crtimprt.exe and you receive subsequent errors:
"CertFindCertificateInStore failed", "CertAdd Failed" and
"AddCertToStore Failed".
This error may occur when there is a mismatch between the PVK file and
the PKCS#7 file. In other words, the private key and the public key do
not correspond. Make sure you copied the correct usercrt.p7b
and userkey.pvk files to your Pocket PC. Also make sure that
you are not mixing files from two different certificates.
You can check this by running the following commands which should show
the exact same number twice:
openssl x509 -modulus -noout -in usercrt.pem
openssl rsa -inform PEM -noout -modulus -in userkey.pem
You might also get the "CertFindCertificateInStore failed" error when
the PKCS#7 file (usercrt.p7b)
does not contain a personal certificate, or is empty. You can check
this by running the command:
openssl pkcs7 -in usercrt.p7b -print_certs -noout
Normally you should see two certificates listed (perhaps three if you
root CA is using an intermediate CA). For instance, the
sample usercrt.p7b file included with crtimprt.zip
contains these two certificates:
subject=/C=NL/ST=ST/L=L/O=TESTORG/CN=TESTUSER
issuer=/C=NL/ST=ST/L=L/O=TESTORG/CN=TESTCA
subject=/C=NL/ST=ST/L=L/O=TESTORG/CN=TESTCA
issuer=/C=NL/ST=ST/L=L/O=TESTORG/CN=TESTCA
Try to import the sample certificates included with crtimprt.zip,
i.e. the files usercrt.p7b and userkey.pvk. Be sure
to use a different container name every
time you import a certificate. If this works, there must be something
wrong with (the conversion of) your certificate.
Don't forget to delete the (sample) certificates you don't need, once
you got it
working.
9.3 Problem: "CryptAcquireContext
Failed"
If you get this error, it means that a problem was detected
even before the private key or the certificates were read. So the usercrt.p7b
or
the userkey.pvk file are not to blame.
Did you change CERT_STORE
or KEY_PROVIDER_NAME in the crtimprt.cfg file, by
any chance? Normally it is not needed to change these parameters. You
can leave these set to the default
value.
One user reported that he had to hard reset his Pocket PC. Then this
error disappeared. Perhaps the certificate store was hosed.
9.4 Known problem with Smartphone
2003
You managed to import a Personal Certificate on
Smartphone 2003 but when you use Pocket Internet Explorer (PocketIE) to
connect to a website that requires certificate authentication, you get
an HTTP error ("403.7 Forbidden: Client certificate required").
This is a known issue in the Internet support functionality (WININET)
in Smartphone 2003, according
to Marcus Perryman from Microsoft. I take it that the Personal
Certificate can still be used for EAP-TLS and L2TP/IPsec VPNs but I am
not sure because I do not own a Smartphone. There is also a Usenet
discussion about this problem.
Back to Contents
10. Advantages
and
disadvantages
Crtimprt has similar advantages
and
disadvantages as P12imprt. Plus:
Advantages of Crtimprt:
- It is much smaller as the other programs, P12imprt and PFXimprt.
- Crtimprt might work on other Windows CE devices such as
Pocket PC 2002 after a recompile of the source code with eVC++ 3.0 (not
tested).
Disadvantages of Crtimprt:
- PKCS#12 certificate files cannot be directly imported. First they
need to be converted on your PC to an intermediate format. Then
Crtimprt imports these intermediate files to your Pocket PC device. In
other words, it works but there is an extra step involved.
- Crtimprt does not have a fancy GUI. (But neither has the ENROLL
program).
- My source code is a bit of a mess. (But so is the ENROLL program.
I think I even fixed a few bugs in it! :-).
Back
to Contents
11. Crtimprt source code
11.1 Licensing details
The source code of Crtimprt is included in the Zip file as Open Source.
This file contains only the changes that were made by me. It is not
actually the full source code that you need to compile the executable.
For legal reasons I made a
patch against the ENROLL source
code. The ENROLL sample program is included with the SDK
for Windows Mobile 2003-based Pocket PCs and can be found in "Program
Files/Windows CE
Tools/wce420/POCKET PC 2003/Samples/Win32/Enroll". If you apply my
patch against the ENROLL sample code you will have the full source
code. I did not want
to redistribute the modified ENROLL source code because of Microsoft's
EULA which was not terribly clear. For instance, one has to comply
with
a Section 1(d) which does not even exist! Besides, you already have the
ENROLL source code when you install the PPC 2003 SDK. You can
then use a program such as GNU patch (Win32 version) to apply my
patch against the ENROLL code. This will result in the full source code
for Crtimprt.
If you are not able to create the Crtimprt source code using GNU patch,
I have the following suggestions:
- I am more familiar with Unix tools so that is why I turned to the
GNU patch program. If you can recommend another (Windows) tool to
generate a patch then I could give it a spin.
- PPCCertImport
by Kiko Vives is a program which is very similar to Crtimprt. It is not
based on Microsoft code and available under a very permitting BSD
licence.
- I am not an official Windows developer and I don't have any
contacts within Microsoft. But if you can get me any kind of legal
reassurance from Microsoft that I won't be sued for publishing the full
Crtimprt source code, then I would be more than happy to do so.
11.2 Using the source code
The source code of Crtimprt compiles under eMbedded
Visual C++ 4.0. You also need
ServicePack 3 for eVC++ or higher (SP4 recommened). Additionally you
need the "SDK
for
Windows
Mobile 2003 for Pocket PCs". The code will also compile under
Visual Studio 2005. Unfortunately it seems that VS2005 no longer
contains the ENROLL sample code, so you will have to download and
install eVC++ 4.0 and the WM2003 SDK in order to extract the ENROLL
project. Again, I wished I could simply distribute the Crtimprt source
code as a project but Microsoft's licensing rules seem to forbid this.
Most of the patch consist of commenting out code that is not needed.
Even more code could have been removed: the base64 routines are not
needed if I had decided to import certificates in DER format (which is
the default on desktop Windows anyway) instead of PEM format. If your
certificates are in PEM, you can convert them easily with OpenSSL: openssl
crl2pkcs7 -in usercrt.pem -outform DER -out usercrt.p7b. Come to
think of it, much of the Enroll code is fairly straight forward anyway
(except perhaps the parts that deal with the PKCS#7 certificate store)
so should Microsoft sic the lawyers on me for violating the EULA, one
could rewrite the program without Microsoft code. In fact, Kiko Vives
has already made such a program so lawyer-siccing would not have the
intended result.
The
Microsoft documentation says that the CERT_STORE_PROV_PKCS7
flag is not supported by the
CertOpenStore()
function on any Pocket PC device. This means that ENROLL and Crtimprt
should not work on any device! In practice however, Crtimprt does seem
to work on most models.
My apologies for the sloppy code. It looks too much like Unix code.
What it does is read in the PVK file, and strip off the PVK magic word
and other blurb. What remains is a "key BLOB" which is imported using
the CryptImportKey()
system call. Then the PKCS#7 file is read into a buffer. It is
converted
from base64 to DER and imported using such calls as CertOpenStore()
and CertAddCertificateContextToStore(). The certificate and
private key are associated with eachother using the CertSetCertificateContextProperty()
call.
It's just a quick and dirty hack. Is there anyone with Windows CE /
Pocket PC programming skills who is willing to clean it up?
Back to Contents
12. Web enrolment
Below is the web enrolment technique. I mention it here only for
the sake of completeness, because I find it a bit too limited and much too
convoluted. Skip to the next section if you
are not interested. Web enrolment on Pocket PC devices is also
described on MSDN
(here
and here).
Web enrolment on Windows 200x uses ActiveX, which is only supported
by
desktop Windows versions. Microsoft has come up with the following
solution for Pocket PC: a separate
ENROLL program for PPC which sends a certificate request to the
webserver and retrieves the certificate from it after the CA has issued
it.
The procedure is as follows:
- Install IIS on your Windows 200x Server.
- Install CA
Services on Windows 200x Server.
- According to the Windows Help file, if you installed IIS after
installing CA services, you need to run "certutil -vroot".
- The Windows 200x server must be configured to immediately issue
certificates (no human interaction required), otherwise the client will
abort the web enrolment procedure. Open Certificate Authority (mmc
certsrv.msc), open the properties of your CA, click the tab
"Policy module ", click Properties, pick "Follow the setting in the
certificate template, if applicable. Otherwise, automatically issue the
certificate".
- You may have to load the Authenticated Session and User Signature
Only templates.
- Test your certificate web enrolment setup by using a browser on
a desktop PC. Obtain any type of certificate by surfing to :
http://11.22.33.44/certsrv where 11.22.33.44 is
the IP address of your Windows Server
Check in Certificate Authority (mmc certsrv.msc) that the test
certificate has been issued. It should be in the "issued" folder, not
in
"pending", "revoked" or "failed".
- Next, you need to repeat this but now with the Pocket PC. As
mentioned earlier, Pocket Internet Explorer is not up to the task. You
need a special program to obtain the certificate.
- On your client host PC, compile the ENROLL sample files included
with the Pocket PC 2003 SDK.
- Copy ENROLL.EXE and ENROLL.CFG to the Pocket PC device. (If you
use the emulator you can use the menu option "Folder sharing". An
emulated Storage Card containing that directory will be created).
- Edit the ENROLL.CFG file: change the server address and enter
Windows 200x's server name/IP address. Also enter the name and password
of the user account on the Windows 200x server (will be sent
unencrypted(!) over the network so that the rightful owner obtains the
certificate).
- Run ENROLL.EXE
- The program will generate a private key, stores it in its
certificate store. It also generates a CSR and submits it to the
Windows
200x server.
- The certificate gets issued. ENROLL.EXE should report "Cert
Has Been Added Succesfully". If you go to Settings -> System
-> Certificates, the certificate should be listed. The root
certificate should also be listed in the Root store.
- The "SubjectName" of the certificate is set to
"SubjectName-Should Be OverWritten by CA". But the CA does not
overwrite
the SubjectName. See #define CERT_SUBJECT_NAME in crypt_web.cpp.
Might be a bug, or perhaps I forgot to change
some setting in Microsoft
Certificate Services.
The procedure did not work for me when I tried to enrol at a Windows
Server
2003 R2. I got a "Cert Denied!" error with a dump of the HTML code that
could
not be parsed.
There might be a way to get certificates without using the ENROLL.EXE
program. This goes by proxy of a desktop Windows machine. On the Pocket
PC you use Pocket Internet Explorer to surf to http://11.22.33.44/certsrv.
Then you save the certificate request to a PKCS#10 file. The PKCS#10
file is transferred to the desktop PC and there submitted to the CA.
The
certificate is then transferred to the Pocket PC and installed. (From
the lack of details you can notice that I have not tried this myself).
Back to Contents
13. Discussion
13.1 Importing PKCS#12 files directly
Windows
Mobile 5.0 was released in 2005 and it supports the PFXImportCertStore()
function. This means that it can import PKCS#12
files directly. This programming interface was absent in
all
previous versions of Windows Mobile so this is why I made Crtimprt.
Windows Mobile 5.0 still does not have an option to
import PKCS#12 certificates, but it is supported in Windows Mobile 6.
Of course, since PFXImportCertStore() is now supported in
Windows Mobile, you can write a program
that imports a certificate from a PKCS#12 file. Another option would be
to write a program so that you can tap a .P12 or .PFX file in File
Explorer on Windows Mobile and then import the file (like on
desktop
Windows). This would require a context menu extension handler for File
Explorer.
I have now made a program that can import
PKCS#12 files directly on Windows Mobile 2003 and Windows Mobile
devices. P12imprt
has been tested on the
Windows
Mobile emulator and a number of actual Windows Mobile devices. The
GUI of the program is minimal.
13.2 Misc. remarks
The web enrolment procedure described above
is very convoluted. The
Crtimprt approach seems better, if you prefer a non-Windows CA and VPN
server.
An even better solution would be to write a program with which you
can import a PKCS#12 file. Then you can avoid several cumbersome
conversion steps. Unfortunately, Microsoft has crippled the Pocket PC
CryptoAPI: they conveniently left out PfxImportCertstore() and
similar routines in Pocket PC 2003 and earlier, possibly due to space
constraints on the PPC (or perhaps
because
of some other strategic reason -- who knows?). They also
left out a PKCS#8 private key import option. So my idea was to use
the
Windows CE port of OpenSSL. OpenSSL has been ported to Windows CE
(and thus also Pocket PC) by Steven Reddie. The result of this approach
is P12imprt. There are also other programs
available on the Internet that can import certificates, such as this
one, but these probably don't work on Pocket PC or can only import
certificates and no private keys.
I get the impression that Pocket PC 2003 does not actually delete the
private key when you use the Certificates applet to delete a particular
certificate from the "Personal" certificate store. If this is true, it
might be a security problem. Note that Microsoft has removed the "Delete"
button in
Pocket PC 2003 Second Edition, Windows Mobile 5.0 and higher. In these
new Windows Mobile versions you can delete a (personal or root)
certificate by tapping and holding the name in the list.
Crtimprt has been reported to work on Pocket PC Phone Edition as such
as the O2 XDA, the iPAQ 6315 and the RoverPC S1. It may also work with
other Pocket PC
hardware such as Windows Mobile-based
Smartphones (Orange SPV etc.) but I am not sure. Send me one and I'll
test it :-).
I would not be surprised if Crtimprt can be used for other Windows CE
devices as well, such as Pocket PC 2002. But I have not tried this. You
will probably need a different compiler than eVC++ 4.0. According to an
MSDN article, Windows CE .NET 4.2+ has a "control
panel utility" that can import a certificate and a private key in
PVK format but this utility is not included with PocketPC. PPC2003
Second Edition (released in 2004) still cannot
import a certificate from a file.
Crtimprt can be used for 802.1x/EAP-TLS. I have received reports that
it works but I have not tested it personally.
EAP-TLS is supported by many vendors. It requires certificates for both
the server and users. Some other EAP authentication protocols such as
LEAP
(Cisco), PEAP (Microsoft) and TTLS (Funk) also require certificates but
only for the server, not for users. In those cases you do not need
Crtimprt: you either buy a server certificate from one of the five CAs
configured in Pocket PC 2003 (Cybertrust,
GlobalSign, Entrust, Thawte, Verisign) or you use File Explorer to
install your own CA certificate.
Back to Contents
14. NetFront browser
The NetFront
browser for Pocket PC ships with a built-in
certificate
manager. You can access it under the menu 'Tools -> Browser
Setting -> Security'. The NetFront certificate manager can import
PKCS#12 files, single (root) certificates in DER format, multiple
(root) certificates in PKCS#7 format and private keys (not sure what
format). NetFront is commercial but a time-limited and crippled version
can be downloaded for free.
Unfortunately the NetFront certificate manager is separate from the Pocket
PC native
certificate applet. So if you import a (personal or root)
certificate with NetFront, the certificate can only be used by NetFront
itself. The certificate cannot be used by Pocket IE, L2TP/IPsec or
EAP-TLS.
The NetFront certificate manager can be a great alternative to
Crtimprt if you are already unhappy with Pocket IE and you only want to
use web client authentication.
Back to Contents
15. Acknowledgements and disclaimers
Thanks to Aleksander Martin, Valery Pryamikov, Andreas Steffen,
Kiko Vives and Steve from Cambridge for their help! One person wished
to remain anonymous. He reported to me that he had made a program
similar to Crtimprt but unfortunately he could not release his
implementation due to company policy. Thanks also to the anonymous
Microsoft employee(s) (Igor D.?) who made the ENROLL sample program
(though they
should have included a certificate import utility in Pocket PC
in the first place).
My crack team of lawyers advised me to include the following text. This
page shows screenshots of an iPAQ device but this does not
necessarily mean an endorsement of or by HP/Compaq. I disclaim
everything anyway :-). Windows,
Windows Mobile, Pocket PC and Windows CE are trademarks of Microsoft Corporation.
The author of this webpage is not associated with Microsoft or any
other company mentioned on the page. All
trademarks are owned by their respective companies.
Back to Contents
16. Revision history
Jun 6, 2006: Released v0.3. Imported certs now also work with
S/MIME.
May 24, 2006: Also runs on Windows Mobile 6.
Feb 8, 2006: Created P12imprt:
import PKCS#12 files on both Pocket PC 2003
and Windows Mobile 5.0!
Jan 31, 2006: Created PFXimprt:
you can now import PKCS#12 files on Windows Mobile 5.0!
Aug 8, 2005: The NetFront browser for Pocket PC can import
certificates, but only for its own use.
May 30, 2005: Crtimprt runs on Windows Mobile 5.0 (on
the emulator, at least).
May 18, 2005: Some Windows
CE devices apparently do
ship with a certificate
panel utility. But Windows
Mobile 5.0 Pocket PC devices do not.
Unknown if they support PFXImportCertStore().
May 12, 2005: Windows
Mobile 5.0 announced. Supports PFXImportCertStore()!
New emulator
released.
Apr 4, 2005: Known PocketIE problem with SmartPhone 2003.
Dec 26, 2004: Uploaded v0.2, mainly due to expired sample
certs in v0.1.
Nov 24, 2004: Added Troubleshooting section.
Oct 14, 2004: movianMail will be discontinued from Oct 31,
2004.
Oct 3, 2004: Some Toshiba Pocket PC models ship with a
certificate import tool. Kudos!
Mar 25, 2004: PocketPC 2003 Second Edition and eVC++ SP3
released: no visible changes in the VPN client.
Feb 23, 2004: Professional Edition (iPAQ 1900 series and
upgraded
PPC2002 models) does not support L2TP/IPsec.
Feb 20, 2004: Linked to Kiko Vives' webpage which contains a
similar program.
Feb 12, 2004: Extract user and CA certs separately from PKCS#12.
The .p7b file should also contain the CA cert(s).
Jan 16, 2004: Previously reported problem does not occur
when
connecting to Windows Server 2003 L2TP/IPsec server. Bug is not in
Crtimprt.
Dec 28, 2003: Everything works! But there is a problem with some
certificates when connecting to Openswan. Packet fragmentation?
Jacco de Leeuw
